Pawn Storm using spear and website phishing
Yesterday Trend Micro released a white paper detailing comprehensive attacks launched against specific targets including ACADEMI (formerly Blackwater), the French Ministry of Defence, and the Vatican Embassy in Iraq. The attacks used a combination of techniques including spear phishing and website phishing. The aim of the campaign was to steal sensitive information from selected individuals in targeted organisations. The campaign has been named Operation Pawn Storm after the famous chess manoeuvre.
The aim of the phishing campaign was to install Sednit malware on the victim PC. Sednit can log keystrokes, send back a list of installed software to a remote server, and execute arbitrary commands on the victim PC. Sednit can also be used to steal personal information from the victim PC. It can download files from a remote host to the victim PC.
Figure A illustrates a Sednit Infographic.
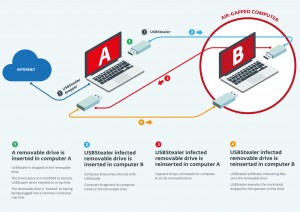
Targets of the phishing campaign were not chosen at random. Selected individuals in targeted organisations received carefully crafted emails. Often the emails would refer to an event that was in the news at the time. The Asia Pacific Economic Cooperation (APEC) conference was used in one such instance. Another event used by the attackers was the MH17 tragedy. Several Polish government officials received emails with an infected attachment called “MH17.doc”. The attachments took advantage of known exploits to install the malware on the victim PC.
A second type of attack utilising phishing websites was also noted in the paper. The attackers in this case created false websites that were typographically very close to genuine websites. One website targeted by the attackers was the academi.com site, used by ACADEMI employees to access Outlook email. The attackers created a domain called academl.com. The spoofed ACADEMI page looked exactly the same as the real one; the only difference was in the domain name. The attackers even used a valid Secure Socket Layer (SSL) certificate for the fake domain.
The attackers in Operation Pawn Storm have shown great persistence and ingenuity and have been conducting their attacks since 2007. The attacks launched have been complex, but have specific targets in mind.
Phishing attacks are probably the most common method used by attackers to gain access to an organisation’s network. The best methods to counter attacks are to keep software up to date, use an up-to-date Anti Virus solution, deploy email filtering, and don’t click on links in an email.
Scott Reeves
MailShark
Free anti-spam service
Free email filter service














