12 New Malware Strains Discovered Each Minute
G DATA researchers discovered a 64.8 percent spike of new malware strains as compared to the first half of 2014. This averages out to 12 new strains per minute. In all, the total number of malware strains this year is expected to be well above the level of 2014, with the U.S., China and France hosting the most malicious and fraudulent websites.
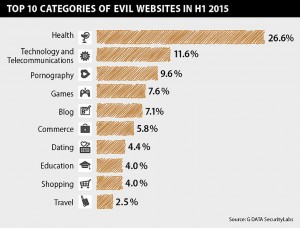
In looking more closely at the banking industry, researchers found that Wells Fargo was the most frequently targeted financial services company by banking Trojans, and the Swatbanker family was the mostly frequently seen banking Trojan in the 6 month period, followed by the ZeuS family.
“About three-quarters of Internet users are conducting their financial transactions online, and cybercriminals have recognized this huge opportunity for malicious attacks,” said Andy Hayter, security evangelist for G DATA. “Not surprisingly, because of this, we’re seeing a significant increase in attacks from banking Trojans for the first time since 2012.”
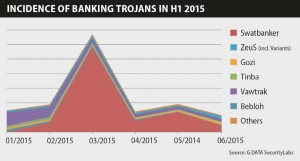
For the first time, websites related to the healthcare industry were most frequently classified as malicious (26.6 percent), with technology and telecom a distant second.
The most commonly seen malware campaign was “Money Rain,” promising various ways to easily acquire money. While this campaign was seen on websites for all of the categories researched, 37 percent of the websites that were clearly connected to Money Rain were in the healthcare industry. Also of note, a new category, personal ads and dating, was revealed to be in the top 10 list of most prevalent malicious and fraudulent websites.
Additional key findings:
- The “Top 10” list of prevented malware attacks is dominated by adware and Potentially Unwanted Programs (PUP). Dealply and Graftor are the most prevalent families in this field.
- Ukraine is new to the Top 10 list of countries most frequently found to be hosting malicious websites with 5% of the activity, putting the country in fourth place. This could potentially be due to the political havoc occurring in this region.
- Exploits for vulnerabilities are now being integrated into exploit kits after just a few days. Users who do not keep their systems up-to-date will easily fall victim to cyber criminals.
- The vulnerabilities in Adobe Flash were most frequently abused to silently and automatically attack and compromise PCs (Exploit).