Banking Trojan delivered to companies via macro-based malware
Cybercriminals continue targeting enterprises with malicious emails whose ultimate goal is to infect company computers with the Dyre/Dyreza banking malware.
But instead of delivering the Upatre downloader to function as the way in for Dyre, the latest email runs take advantage of another successful approach that has lately become popular again: documents carrying macro-based malware.
The emails – posing as notices of failed ACH and wire transfers, fake alerts of delivered fax messages and parcels, or invoice and billing statements – ask the recipients to follow a link embedded in the email which ostensibly points to details about the transaction or message.
Actually, the link leads to a file hosted on a Dropbox page, which contains instructions for users to enable the macros to view the file (click on the screenshot to enlarge it):
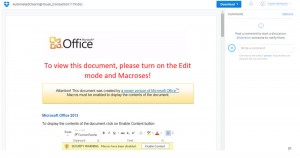
By doing that and downloading and running the file, the victims actually run the Bartalax dropper, which then downloads and installs the Dyre Trojan.
According to Trend Micro, most Bartalax victims are located in the US, Canada and Australia.
“Dropbox and other cloud-based services are known to host malware and cybercriminals’ C&C software, but this is the first time we’re seeing Dropbox used to host macro-based malware, which is rapidly increasing despite its being a thing of the past,” says fraud analyst Christopher Talampas. “We have already contacted Dropbox about the more than a thousand links hosted on their site.”
“Addressing macro malware in an enterprise (and small and medium-sized business) setting involves reevaluating and revisiting existing security policies,” he advises.
“It’s also advisable to decrease the attack surface area by making sure systems within the corporation have the necessary security measures in place: for instance, it may be wise to disable Windows Scripting Host on users’ systems if it serves no substantial purpose. Lastly, user education will go a long way in defending against these types of threats, in particular, those that exploit human error, e.g., enabling malicious macros in Word documents.”