New add-ons found in Dyre malware
Dyre malware re-surfaced recently with a new version that contains several new features that are designed to capture more information from the victim computer and from the organisation targeted.
Figure A illustrates how Dyre works.
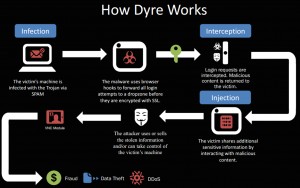
Dyre (also known as Dyreza) was first detected in June 2014. Investigators uncovered it when researching a phishing campaign targeting several financial institutions. Dyre was of particular concern, as it was able extract submitted login data prior to encryption. The initial entering of login credentials is not encrypted until the user actually clicks a login button. Dyre can capture the information just before the credentials are entered i.e. before the login button is clicked.
The method of attack was to send users an email that stated either that a payment was rejected, or that an invoice was attached. The attachment to the email was a zip file. When opened it would install Dyre.
A blog post at Phishlabs this week detailed a new version of Dyre with several additional features. One of the new capabilities is a browser snapshot. This feature can capture cookies, private keys and client side certificates. This means that the attackers can potentially use the victim’s credentials when conducting fraudulent activities.
Another capability added is to send a list of start-up programs and a list of running programs to a remote host. This is a specific feature that is designed with corporations in mind; it allows the attacker to masquerade as the victim computer, and it means that an attacker can compile a list of software used by an organisation, with a view to exploiting known vulnerabilities.
Finally, the new version has enhanced command and control communication features. Dyre has the capability to use Secure Socket Layers (SSL) to encrypt communications to the malicious server. This makes Dyre difficult to detect by monitoring network traffic alone.
As with the earlier variants of Dyre, the primary means of attack is via phishing emails. The emails appear to be from well known companies and appear legitimate. Phishing emails are a low tech but effective way to spread malware. Avoid clicking on links in emails or opening zip files attached to emails.
Scott Reeves
MailShark
Free anti-spam service
Free email filter service