Malvertising set to wreak one BILLION dollars in damage this year
Records have fallen as malvertising clocked its most prolific month in history, making it one of the biggest threats to endpoint security.
If the scourge continues, criminals will have inflicted a billion dollars in damages by the end of the year from a paltry US$12,000 investment, according to researchers at security firm Invincea.
In this threat report, the firm says it blocked some 2100 malvertising attacks against its customers.
It says the attacks represent 2.1 million malicious advertisements purchased by maldoers.
“June was by far the worst month on record for malvertising – likely due to the multiple Flash zero-day exploits that were integrated into exploit kits used to host fraudulent ads that month”, the report says.
“At an industry average price of approximately US$2.90 per thousand online ads, malicious actors were able to inflict more than half a billion dollars of damage for a mere US$6,000 in advertising spend.
“On an annualised basis, the malvertising campaigns Invincea observed generate more than $1 billion in damage per year.”
Malvertising is the vector by which threats like ransomware, click-fraud botnets, and banking trojans such as Zbot are delivered.
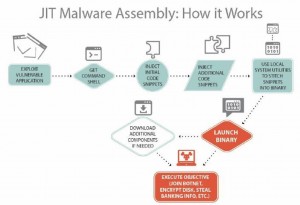
Researchers also found an upswing in just-in-time malware in which the malicious executable is assembled on a target’s machine rather than beforehand in a bid to evade whitelists and network sandbox analysis.
The just-in-time technique works with an exploit targeting the likes of Adobe Flash or Office wares and employs tools such as powershell, host scripting, and VBScript assembly. It can run from disk as an executable or within memory.
“Threat actors are now having great success in evading network sandbox, IDS, and traditional endpoint security solutions with this multi-stage delivery assembly approach,” boffins say.
Weaponised Office documents are also within the top threat vectors so far this year which have become plug-and-play thanks in part to oft-reused VB scripts.
This article first appeared on The Register with the original article found here.