SMTP being used for Shellshock attacks
Shellshock is refusing to go away. Over the last few days a new method of attack using Simple Mail Transport Protocol (SMTP) has been detected. The aim of the attackers is to use the Shellshock exploit to conduct Distributed Denial of Service (DDoS) attacks via botnets.
The Shellshock vulnerability was first disclosed by US-CERT on 24/9/2014. Figure A shows the officially recorded timeline.
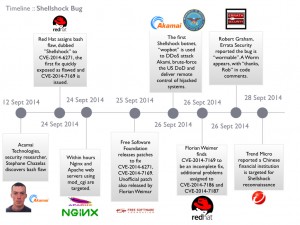
The bug had existed in the bash shell for approximately 25 years; it allowed an attacker to inject code into a bash shell and potentially gain control of a server. Disclosure of the bug caused a flurry of activity on the part of developers (to patch the bug) and attackers (to exploit the vulnerability). Fortunately, the developers managed to release several patches before wide scale attacks occurred. Most organisations managed to patch vulnerable systems in a timely manner. The systems affected were UNIX based systems, including Linux and Mac OS X.
It was quite possibly only a matter of time before SMTP was used to craft Shellshock attacks. The Fire Eye blog listed several potential methods of attack in a blog post dated 27/9/2014. Amongst the attacks mentioned is installation of a Perl script (called Shellbot) that uses IRC to communicate to a remote host. Shellbot can be used to conduct DDoS attacks by either building or joining existing botnets. Two variants of Shellbot are listed on the blog.
Other exploits mentioned include stealing the /etc/passwd file and using email to detect if a host is vulnerable to Shellshock. As the author notes, the email probe was unique in its method of attack. Now that particular vector of attack has been detected, with servers being targeted in the United States. The exploit used for the SMTP attacks uses malicious code in the header field to download and install a script in the /tmp directory. A sample of the exploit is shown below.

A second type of malware has also been detected by AlienVault. This malware looks to send details about the machine to a remote attacker, as well as joining botnets with the aim of launching DDoS attacks.
Several Mail Transport Agents (including Sendmail and Qmail) are affected by this new Shellshock exploit. Applying the bash patches will remove the risk of the Mail Transport Agent being affected.
The bash vulnerability was labelled as high risk when first disclosed because of the widespread use of the bash shell in Linux and UNIX machines. The latest Shellshock attack vector is a timely reminder that patching of mail servers running Linux or UNIX should be expedited.
Scott Reeves
MailShark
Free anti-spam service
Free email filter service