US-CERT warning over Dyre banking malware
The Dyre phishing campaign is continuing apace, to the extent that the US-CERT has now issued a warning containing specific details of the threat. Dyre is using two old vulnerabilities in Adobe reader to install itself on victim PCs, with a phishing campaign being used as the attack vector. US-CERT has stated that the Dyre phishing campaign has been going since mid-October 2014.
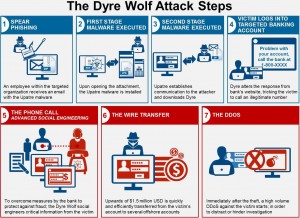
Dyre (also known as Dyreza) malware can steal login credentials, modify network traffic and communicate via encrypted channels with a command and control server. The method the attackers use is to send a phishing email with an infected PDF attachment. The Dyre malware looks to exploit two old vulnerabilities in Adobe Reader. These are CVE-2013-2729 and CVE-2010-0188. Both these vulnerabilities have patches; the first vulnerability had a patch issued on 14 May 2013, whilst the second had a patch released on 16 February 2010.
Dyre has a number of capabilities that include “browser hooking”. This technique means that Dyre can steal login credentials before they are encrypted. Dyre also compiles a list of running and installed software on a victim’s PC and sends this information to cyber attackers. This enables attackers to craft further attacks, based on specific software vulnerabilities.
US-CERT has indicated that the email will contain a subject line with “Unpaid invoice”. The attachment will be called Invoice621785.pdf, or similar. Upon installation, the malware masquerades under the moniker “Google Update Service”.
To guard against such attacks, it is recommended that users keep all software up to date, with the latest patches installed. Email filtering is very effective at filtering out phishing emails, and should be used in conjunction with up to date Anti Virus software. Finally, a reminder should be sent to users to not open attachments unless they have confirmation of the validity of the email, and to not follow links in emails.
Scott Reeves
MailShark
Free anti-spam service
Free email filter service